Introduction
In Kubernetes RBAC is a method for controlling access to resources based on the roles assigned to users or service accounts within the cluster. RBAC helps to enforce the principle of least privilege, ensuring that users only have the permissions necessary to perform their tasks.
Kubernetes RBAC best practices
Kubernetes create Service Account
Service accounts are used to authenticate applications running inside a Kubernetes cluster to the API server. Here’s how you can create a service account named huupvuser:
kubectl create sa huupvuser
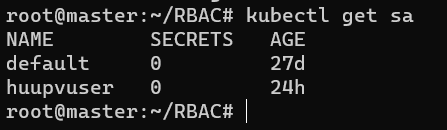
kubectl get sa
The result is as follows:
Creating ClusterRole and ClusterRoleBinding
Creating a ClusterRole
A ClusterRole defines a set of permissions for accessing Kubernetes resources across all namespaces. Below is an example of creating a ClusterRole named test-reader that grants read-only access to pods:
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: test-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]Apply the ClusterRole:
kubectl apply -f clusterrole.ymlCreating a ClusterRoleBinding
A ClusterRoleBinding binds a ClusterRole to one or more subjects, such as users or service accounts, and defines the permissions granted to those subjects. Here’s an example of creating a ClusterRoleBinding named test-read-pod-global that binds the test-reader ClusterRole to the huupvuser service account:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: test-read-pod-global
subjects:
- kind: ServiceAccount
name: huupvuser
apiGroup: ""
namespace: default
roleRef:
kind: ClusterRole
name: test-reader
apiGroup: rbac.authorization.k8s.ioApply the ClusterRoleBinding:
kubectl apply -f clusterrolebinding.yaml
Combined Role YAML
For convenience, you can combine the ClusterRole and ClusterRoleBinding into a single YAML file for easier management. Here’s an example role.yml:
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: test-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: test-read-pod-global
subjects:
- kind: ServiceAccount
name: huupvuser
apiGroup: ""
namespace: default
roleRef:
kind: ClusterRole
name: test-reader
apiGroup: rbac.authorization.k8s.io
Apply the combined YAML file:
kubectl apply -f role.yml
Verify ClusterRole and ClusterRoleBinding:
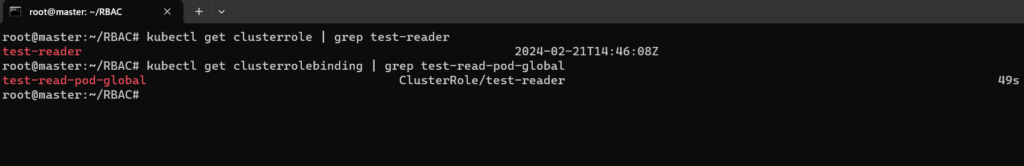
kubectl get clusterrole | grep test-reader
kubectl get clusterrolebinding | grep test-read-pod-globalThe result is as follows.
Delete ClusterRole and ClusterRoleBinding:
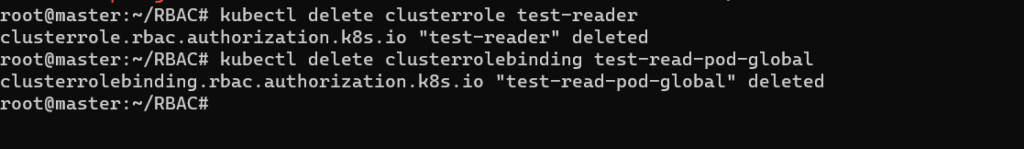
kubectl delete clusterrole test-reader
kubectl delete clusterrolebinding test-read-pod-globalThe result is as follows.
Conclusion
we’ve explored the basics of Role-Based Access Control (RBAC) in Kubernetes RBAC best practices. Through the creation of Service Accounts, ClusterRoles, and ClusterRoleBindings, we’ve demonstrated how to grant specific permissions to users or service accounts within a Kubernetes cluster.
RBAC is a powerful mechanism for ensuring security and access control in Kubernetes environments, allowing administrators to define fine-grained access policies tailored to their specific needs. By understanding and implementing RBAC effectively, organizations can maintain a secure and well-managed Kubernetes infrastructure. I hope will this your helpful. Thank you for reading the DevopsRoles page!
