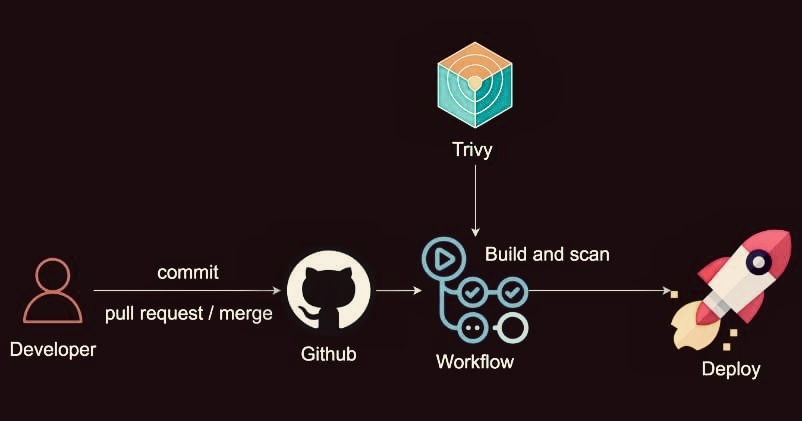
Ensuring security within your Continuous Integration and Continuous Deployment (CI/CD) pipeline is crucial for modern software development. This detailed guide will help you integrate Trivy with GitHub Actions to automate CI/CD Security Scanning in your workflow.
Table of Contents
What is Trivy?
It is a comprehensive vulnerability scanner for container images, file systems, and Git repositories. It can detect vulnerabilities, misconfigurations, secrets, and licenses across various platforms. Trivy is simple to use and integrates well with CI/CD tools like GitHub Actions.
Setting Up GitHub Actions for CI/CD
GitHub Actions is a powerful automation tool that allows you to create custom workflows for your projects. These workflows can run on events such as pushes, pull requests, and merges. To integrate Trivy into your GitHub Actions workflow, follow these steps:
Step 1: Create a GitHub Repository
Start by creating a GitHub repository if you don’t already have one. Initialize it with your project files and include a .github/workflows directory for your GitHub Actions workflows.
Step 2: Define Your Workflow File
Create a workflow file in the .github/workflows directory and name it ci.yml. This file will define the steps GitHub Actions will follow to build, test, and deploy your project.
name: CI/CD Pipeline
on:
push:
branches: [ main ]
pull_request:
branches: [ main ]
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Set up Docker Buildx
uses: docker/setup-buildx-action@v1
- name: Build Docker image
run: docker build -t my-app .
- name: Scan image with Trivy
uses: aquasecurity/trivy-action@master
with:
image-ref: my-app
- name: Deploy to production
run: echo "Deploying application..."Step 3: Workflow Breakdown
- Checkout Code: This step uses the
actions/checkout@v2action to clone your repository. - Set up Docker Buildx: This step sets up Docker Buildx to enable multi-platform builds.
- Build Docker Image: This step builds your Docker image using the Dockerfile in your repository.
- Scan Image with Trivy: This step is the
aquasecurity/trivy-actionto scan the built Docker image for vulnerabilities. - Deploy to Production: This is a placeholder step where you can add your deployment commands.
Step 4: Commit and Push Your Workflow
Commit your ci.yml workflow file to your repository and push the changes. This will trigger the GitHub Actions workflow to run.
git add .github/workflows/ci.yml
git commit -m "Add CI/CD workflow with Trivy scanning"
git push origin mainMonitoring and Reviewing Results
After pushing your workflow file, navigate to the “Actions” tab in your GitHub repository. You will see your workflow running. GitHub Actions provides logs and details for each step, including the Trivy scan results.
Benefits of Integrating Trivy in CI/CD
1. Automated Security Scanning
By integrating Trivy into your CI/CD pipeline, you ensure that every code change is automatically scanned for vulnerabilities. This helps in identifying and addressing security issues early in the development process.
2. Continuous Compliance
Automated scanning helps maintain compliance with security standards and regulations. It ensures that your software meets security requirements before deployment.
3. Improved Security Posture
Regular scanning and fixing vulnerabilities improve the overall security posture of your application. This reduces the risk of security breaches and ensures a more secure deployment.
FAQs
Q1: What is Trivy?
A1: Trivy is a comprehensive vulnerability scanner for container images, file systems, and Git repositories that detects vulnerabilities, misconfigurations, secrets, and licenses across different platforms.
Q2: How does Trivy integrate with GitHub Actions?
A2: Trivy integrates with GitHub Actions by adding a step in your GitHub Actions workflow file to scan Docker images for vulnerabilities.
Q3: What are the benefits of using Trivy in a CI/CD pipeline?
A3: Using Trivy in a CI/CD pipeline ensures automated security scanning, continuous compliance, and improved security posture by identifying and fixing vulnerabilities early in the development process.
Q4: How can I monitor the results of Trivy scans in GitHub Actions?
A4: You can monitor the results of Trivy scans in GitHub Actions by navigating to the “Actions” tab in your GitHub repository and reviewing the logs and details for each step of the workflow.
Conclusion
Integrating Trivy with GitHub Actions for CI/CD security scanning is a straightforward process that provides significant benefits. By automating vulnerability scanning, you can ensure that your applications are secure and compliant from the earliest stages of development. Follow the steps outlined in this guide to set up your own secure CI/CD pipeline using Trivy and GitHub Actions.
For more detailed documentation and advanced configurations, refer to the official Trivy and GitHub Actions documentation. I hope will this your helpful. Thank you for reading the DevopsRoles page!

