Table of Contents
Introduction
To use Windows Active Directory (AD), Active Directory Federation Services (ADFS), and Security Assertion Markup Language 2.0 (SAML 2.0) to log in to the AWS Management Console, you can follow these general steps How to Use Windows Active Directory, ADFS, and SAML 2.0 to login AWS Console:
- Set up an ADFS server: Install and configure ADFS on a Windows server that is joined to your Active Directory domain. This server will act as the identity provider (IdP) in the SAML authentication flow.
- Configure AWS as a relying party trust: In the ADFS server, create a relying party trust for AWS. This trust establishes a relationship between the ADFS server and AWS, allowing the exchange of SAML assertions.
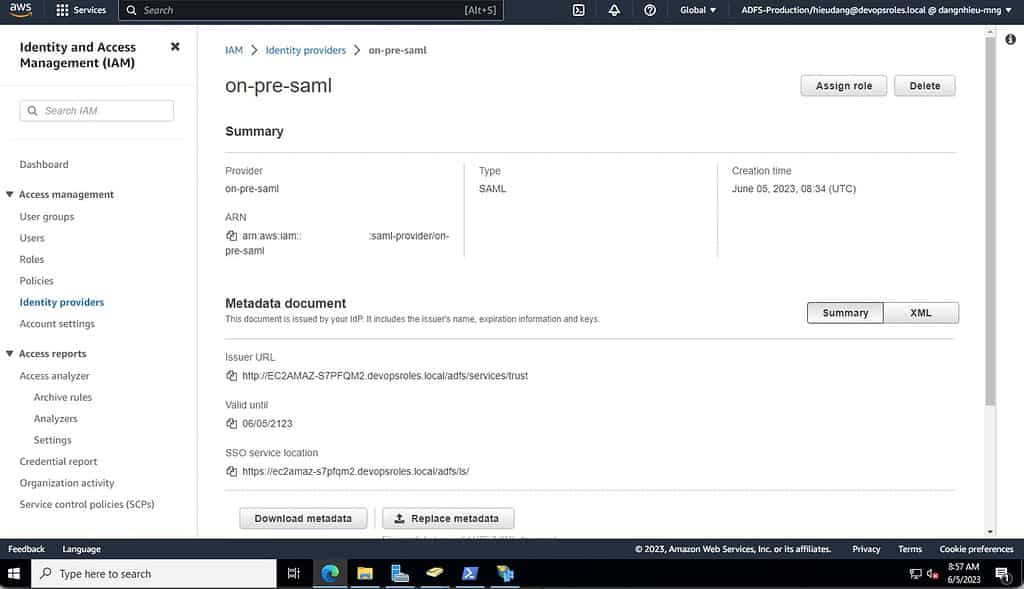
- Obtain the AWS metadata document: Download the AWS SAML metadata document from the AWS Management Console. This document contains the necessary configuration information for AWS.
- Configure claims rules: Set up claims rules in the ADFS server to map Active Directory attributes to the corresponding AWS SAML attributes. This step ensures that the necessary user information is included in the SAML assertion sent to AWS.
- Set up AWS IAM roles: Create IAM roles in AWS that define the permissions and access policies for users authenticated through SAML. These roles will determine the level of access users have in the AWS Management Console.
- Configure AWS IAM identity provider: Create an IAM identity provider in AWS and upload the ADFS metadata XML file. This step establishes the trust relationship between AWS and the ADFS server.
- Create an IAM role mapping: Create a role mapping in AWS that maps the SAML attributes received from ADFS to the corresponding IAM roles. This mapping determines which IAM role should be assumed based on the user’s attributes.
- Test the login process: Attempt to log in to the AWS Management Console using the ADFS server as the IdP. You should be redirected to the ADFS login page, and after successful authentication, you will be logged in to the AWS Management Console with the appropriate IAM role.
What is ADFS and SAML 2.0?
ADFS Overview
ADFS (Active Directory Federation Services) is a component of Windows Server that provides users with single sign-on access to systems and applications located across organizational boundaries.
SAML 2.0 Overview
SAML (Security Assertion Markup Language) 2.0 is an open standard for exchanging authentication and authorization data between identity providers (IdP) and service providers (SP).
When integrated, ADFS acts as the IdP and AWS acts as the SP, enabling users to log in to AWS using their Windows domain credentials.
Benefits of Using ADFS and SAML with AWS
- Centralized identity management using Active Directory.
- Improved security with token-based authentication.
- No need to manage IAM user passwords in AWS.
- Enhanced user experience through seamless SSO.
- Audit trail and compliance alignment with enterprise policies.
Using Windows Active Directory ADFS and SAML 2.0 to login AWS Console
Today, I tried the lab enabling federation to aws using windows active directory adfs and saml 2.0
I have a note for everyone: Use Windows Active Directory, ADFS, and SAML 2.0 to login AWS Console
- The Cloudformation template is an older version and some AMI IDs are older and cannot be used. In my case, I was using the Tokyo area, but I couldn’t use AMI and it crashed.
- Do not use Windows Server 2016 for your AD server. The “Configure AWS as a trusted relying party” step does not succeed and I am unable to log in to the AWS console afterward.
- Cloudformation template does not set up IIS, manual configuration, or create CERT yourself
- If you get an error when you visit the site https://localhost/adfs/ls/IdpInitiatedSignOn.aspx
An error occurred
The resource you are trying to access is not available. Contact your administrator for more information.Change setting of EnableIdpInitiatedSignonPage property:Set-AdfsProperties – EnableIdpInitiatedSignonPage $True
You have finished the lab by logging into the AWS console with the administrator role
External Links
Conclusion
Using Windows Active Directory ADFS and SAML 2.0 to log in to AWS Console. These steps provide a general overview of the process. The specific configuration details may vary depending on your environment and setup. It’s recommended to consult the relevant documentation from AWS and Microsoft for detailed instructions on setting up the integration between ADFS, SAML, and AWS. I hope will this your helpful. Thank you for reading the DevopsRoles page!

